Automatic key-based SSH authentication

Data transfer security is a priority task when using services with remote data access. Authentication on a server with a private key, creation of which does not take much time, provides a user with ultimate privacy. In the following article, we look at the process of key creation and connection to a remote server in Windows and Ubuntu Linux.
SSH protocol allows using authentication by a password as well as by a couple of keys, one of which is kept on a server while another – on a user’s computer. These two ways of authentication have both pros and cons.
Authentication with a Password
For any kind of user authentication including authentication with a password, SSH implements a variety of data transfer security technologies. The password is transferred in an encrypted form over the network, which complicates its possible theft by intercepting network traffic. The password is not kept on a user’s computer, and using a blank password is forbidden by default. As a rule, a server limits the number of password inputs, so using brute-force attack to get the password is ineffective.
Nevertheless, an encrypted data transfer does not protect from weak passwords. Password complexity entirely depends on a user. Too simple password can be easily guessed through social engineering methods, and too complex password can be forgotten by a user. In addition, password access does not allow a server to identify a client accurately. Client authentication is based only on the correctness of a password input in an authentication field.
Advantages of password access:
- easy to use;
- no need for special configuration from a client’s or a server’s side.
Disadvantages:
- security is entirely based on a password complexity and confidentiality;
- accurate client identification is impossible;
- a password can be easily intercepted either through installing spyware from a client’s side or with the help of social engineering.
Since using a password is not able to ensure an absolute security of a client, it is safer to use client authentication with a key when connecting via SSH.
Authentication with a Key
Authentication via SSH (SSH authentication) with the help of a key is much safer than password authentication because it ensures more reliable user identification. During authentication process, two keys are used – public and private. A public key is kept on a server and performs a role of a digital “lock”, which can be opened only with the key that is owned by a user.
If somebody wants to gain access to data on a server, he or she will have to get a user’s digital key. Even if an attacker tries to act as a mediator between a server and a client, the latter will receive a message that host data have been changed and key transfer through a given connection is not safe. One must follow the main rule of security: a private key should be always kept secret. If somebody gets a file with a private key, he or she will be able to get access to a server. And if someone gains access to public keys as a result of an attack on a server, then he can pretend to be a real host.
A private key can be additionally protected with a password. Thus, it will be far more complicated to steal a key because an attacker will have not only to get a unique key pair, but also to find a password to them.
One private key can be used to connect to several servers at the same time. In such a case, one and the same public key is installed on these servers. So, if a client uses password access, he or she does not have to use different keys for different servers or to memorize many passwords.
Advantages of authentication with a key:
- double-sided authentication by a key pair;
- one key pair can be used for several servers at once;
- stealing a key and computing a key pair is highly complicated;
- additional protection of a key file by a password or a physical disk.
Disadvantages of a key pair:
- improper protection of a key file can lead to its possible theft.
Key Generation in Windows OS
To create a key file, you need the PuTTYgen application. You can download it on the official website as a part of the PuTTY bundle. This program will help us to create a key for a client’s authorization and authentication on a server. If you only need to create a key, you can download the PuTTYgen utility alone. Running the utility, you will see the window with input parameters:
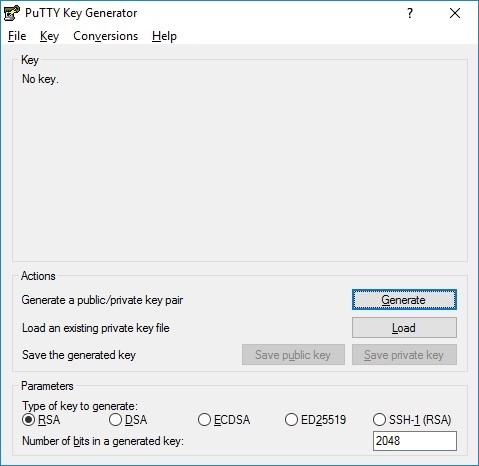
The program starts creating a new key by pressing the Generate button. Then you need to move your mouse or type a set of random characters within the program window for collecting random data. The generated key will differ from the key on the screenshot. The progress bar shows the generation process.
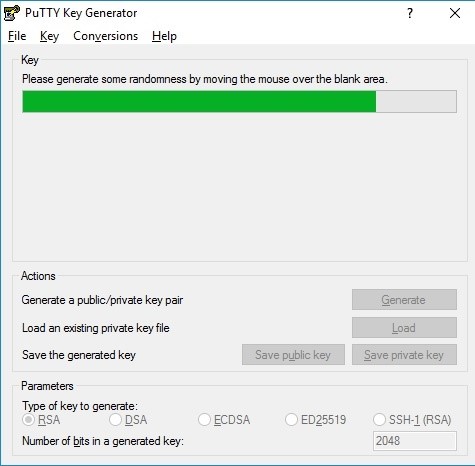
When key generation is over, the program shows you the window containing a public key and the private key fingerprint.
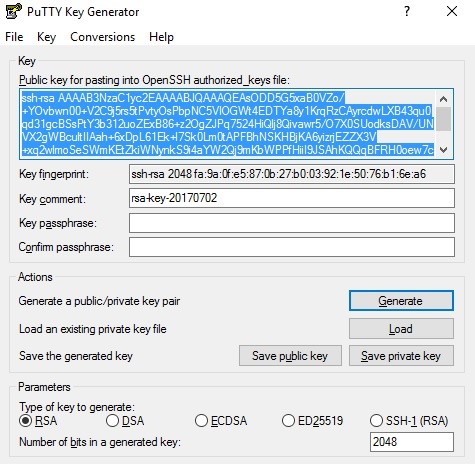
The Public key field contains the public part of the key, which will be kept on a server. In the Key comment field, you can add some comments to the key. If a client has several authentication keys for different servers, he or she can fill in the field a server’s name for which a particular key is used. Key fingerprint is necessary to enhance connection security and accurate host identification. For the first connection, a user will receive a message that a given key has not been previously used for user authentication. If the message has been received for the second time, it means that either public keys have been changed on a server, or somebody pretends to be a host.
In the Key passphrase field, you can enter a password to the key. In that case, a server will additionally request the password when a user is authenticated by the key. To save the created key, press the Save private key button. If no password was set in the Key passphrase field, the program notifies you about it before saving the key.
The key will be saved in the file with the .ppk extension (PuTTY private key). This file should be kept in a safe place protected from the third party access.
Uploading a Public Key to a Server
Now you need to upload the public key to a server so that you can connect to it using the private key. To do this, run PuTTY and connect to a server.
Open the program configurations and choose Session item. In the Host name field, you have to enter the server’s address to which you are going to connect. You can also have to specify a connection port. After filling all the parameters, press Open.
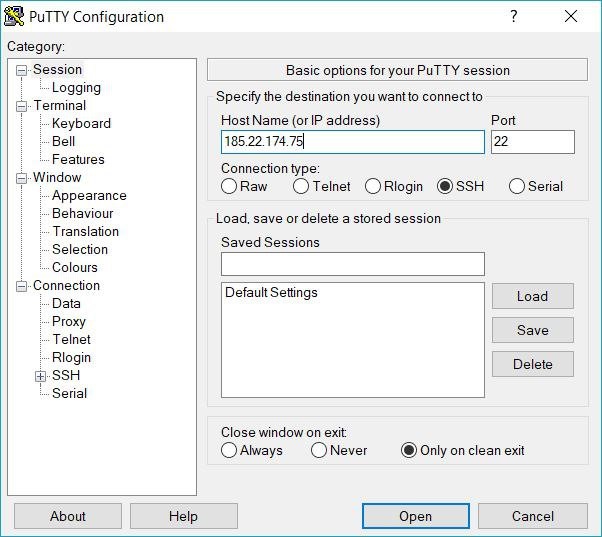
In the opened terminal window, you have to enter a user’s name and a password. In our case, we log in under the root user.
Be careful when entering the password: no symbols are shown while typing!
Keys are kept on the server in the ~/.ssh folder and written in the authorized_keysfile. To add your public key there, you need to edit the file in the nano console text editor, for example. You can open the file using the command:
nano ~/.ssh/authorized_keysIf the program asks you whether you want to edit the file, press Y. If there are other public keys in the file, you will see them in the terminal window.
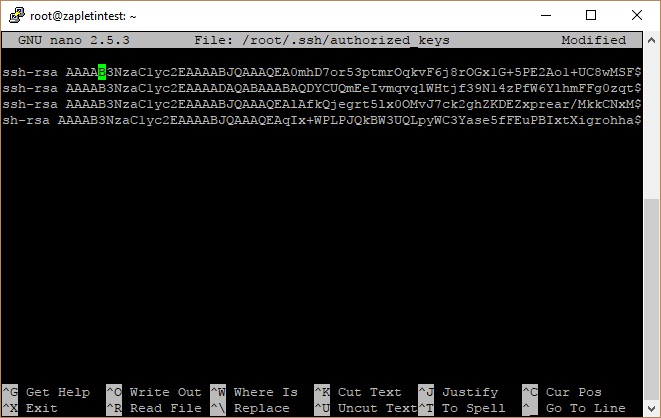
During key generation in the PuTTYgen, the public key part was shown in the Public keyfield. If you did not save the key, open the file with the private key in the PuTTYgen, and the program will generate the public key out of the private one. You should copy and paste it into the nano window. You can do this by clicking the right mouse button.
By pressing Ctrl+X , we exit the editor. The program asks you one more time whether to save the changes in the file. PressY and exit the editor.
So, your public key is saved now in the server’s key file. To use your private key for connection, you need to use the Pageantutility, which is included in the PuTTY bundle. The utility icon will appear in the system tray after you run it. You should either click on it twice and open the agent window, or open the context menu. Choose Add key item and select the key file.
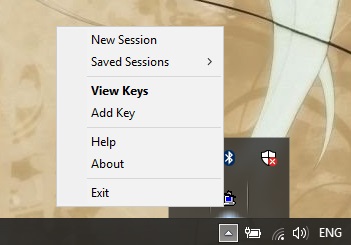
The private key is added to the key base now, so the server will no longer request the password. The agent must be run during authentication.
Key Creation in Ubuntu OS
In Ubuntu, there is no much difference from the key generation in Windows. The PuTTY bundle is available in Ubuntu Linux repositories as well. However, we will create a key by means of another popular utility – OpenSSH.
First of all, let us install the package from the repositories with the command:
sudo apt-get install sshAfter the package is installed, we create a new key by using the command:
ssh-keygen –t rsaThe program asks you to enter the standard parameters: a file name and a password to a private key. The key will be saved by default in the /home/user/.ssh/ directory as two files: id_rsa (the private key) и id_rsa.pub (the public key).
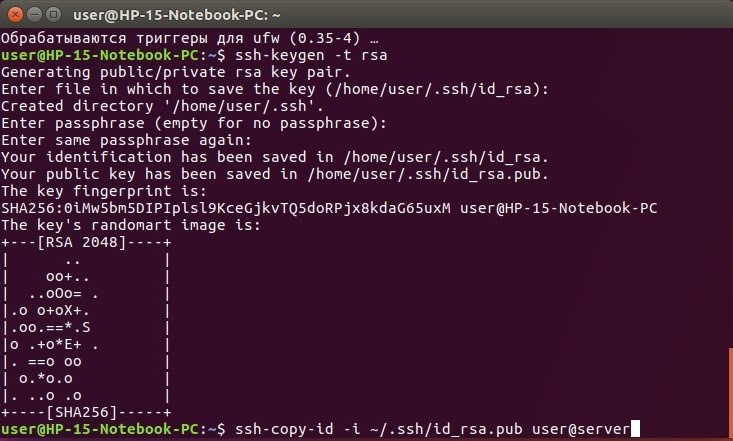
After generation, the program shows the key fingerprint in the terminal window. To upload the key to the server, enter the command:
ssh-copy-id –i ~/.ssh/id_rsa.pub user@serverwhere user is the user name you use for connection to the server, server is your server’s address, and id_rsa.pub is the public key file.
After successful authentication, the terminal welcomes you to the server’s console.
Importing OpenSSH File to PuTTY
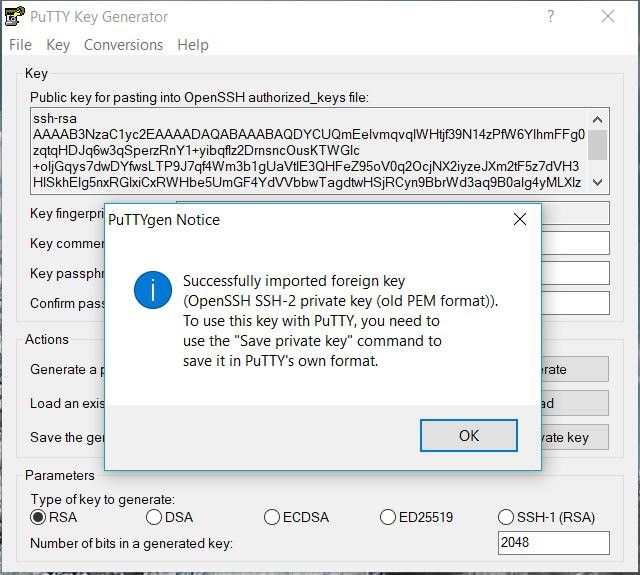
The OpenSSH key file format is different from the PuTTY key format. So, you need to convert the key created in Unix-system in order to use it successfully under Windows OS in the PuTTY client. To do this, you have to run the PuTTYgen and add the key file there.
Choose the key file generated in Unix-system. The program shows you the message that the key has been successfully imported.
To save the key in the format you need, press the Save private key button. Then choose key storage location and the file’s name. Remember that the private key file is to be protected from the third party access!
For authentication on a server with the help of the PuTTY, you need to add your key to the PuTTY agent base (Pageant). How to add the key is described above.
Although using a key pair requires initial configuration and key generation, it makes the following authentication easier and significantly increases connection security. One key file can be used for authentication on several servers. In such a case, one and the same public key should be added on each server.